At present, there are two angles of research on biometric template protection from hardware and software.
The main idea of ​​the hardware solution is to design a closed identification system. The template is stored in a security module. From the physical point of view, the template is guaranteed to be irreversible and unlinkable. Privaris PlusID is a commercial product based on this idea. The product integrates a complete biometric system including a collection device into a key-card-sized device. The biometric template registered by the user is stored inside the device. If the authentication is successful, the device sends out a series of keys. A system like this is called a "system on card." Another similar, but called "match on card," this system encapsulates a template database and matcher into a physical security module, and externally acquired biometrics are input to the device during authentication. Make a match. These hardware-based solutions do indeed protect the security of the biometric templates, but they also weaken the biometrics to the extent that they need to carry the “your own†features, and also limit the scope of application of biometric authentication. As the peripheral authentication technology is used in the terminal, it cannot implement online internal authentication and cannot perform 1:N identification.
Software-based solutions are also called biometric encryption technologies. The insecurity of the biometric template mainly lies in its permanent loss due to its irrevocable reset, while ordinary passwords and keys can overcome this danger through cryptographic processing. In recent years, more and more researchers have devoted themselves to the research of biometric encryption techniques and have proposed various biometric encryption algorithms. An ideal biometric encryption algorithm must satisfy the following requirements: (1) Irreversibility, in any case, cannot be inversely transformed from the biometric template to get the original biometric data; (2) Unlinkability, same biometric use Different algorithms generate different templates and cannot match each other and between the template and the original biometrics. (3) Republishability. Once a biometric template is lost, you can use the same biometric to republish one. Different templates; (4) Accuracy The identity authentication performance of the template satisfying the above three conditions can meet the system requirements.
2. Equipment Certification Technology
In the iris recognition system, once the illegal device is connected to the system, when the iris information is collected, the attacker can use the illegal device here, or open the back door to the device to obtain the original iris image information of the collected person, which brings about great safe question. Therefore, it is necessary for the terminal side to verify the legitimacy of the access device. The device authentication mechanism can ensure that only legitimate terminal devices can access the system, maintain legitimate rights and interests, and protect the security of the iris recognition system.
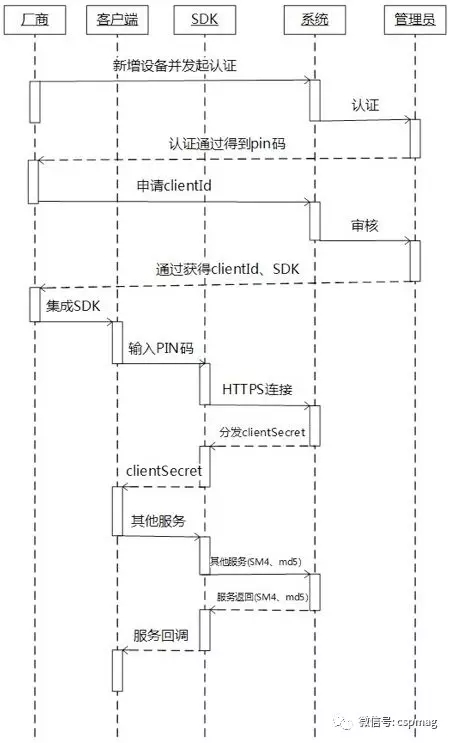
Before device authentication, the device manufacturer first registers with the iris recognition system and submits vendor information to the administrator for review. The device authentication and data transmission timing diagrams are as follows:
Figure equipment certification and data transmission timing diagram
The device authentication service uses HTTPS reliable communication. The manufacturer first adds a device to the system and reports the device-related information to the system. Then the manufacturer initiates an authentication request for the device that needs to be certified in the system. The system employee audits the device, and the certified device system generates a corresponding PIN code. Revised); The vendor develops the client through the integrated SDK and completes device access and subsequent iris image acquisition and uploading.
3. Data encryption technology
Data transmission encryption technology is mainly used to encrypt the data stream in transmission. Commonly used methods include link encryption, node encryption, and end-to-end encryption.
1) Data Storage Encryption Technology
The purpose of the data storage encryption technology is to prevent data loss in the storage link, which can be divided into ciphertext storage and access control. The former is generally implemented through cryptographic conversion, additional passwords, and encryption modules; the latter is the review and restriction of user qualifications and permissions to prevent unauthorized users from accessing data or unauthorized users to access data in the system. Users of different working groups give corresponding rights to protect important data from being accessed by children.
2) Data Transmission Encryption Technology
(1) Link encryption. Link encryption encrypts data at the data link layer just before the physical layer. The receiving party is the node machine on the transmission path, and the information is decrypted and re-encrypted in each node machine, and successively performed until it reaches the destination.
(2) End-to-end encryption. End-to-end encryption is an encryption method that is used to transmit data from one end to the other. The data is encrypted at the sending end and decrypted at the final destination (receiving end). The intermediate node does not appear in clear text. The use of end-to-end encryption is done at the application layer, ie, at the higher layers before transmission. Messages other than headers are all in the form of ciphertext throughout the transmission process.
(3) node encryption. Node encryption is similar to link encryption in terms of operation. All messages are decrypted at the intermediate node and then encrypted. However, unlike link encryption, node encryption does not allow messages to exist in clear text at the network node. It decrypts the received message first, and then uses a different key for encryption. This process is performed on the node. In a security module.
In the process of iris registration and iris verification, when the client (terminal) communicates with the server, the secret SM4 encryption algorithm may be used to encrypt the data, and the MD5 algorithm may be used to sign the data to ensure the security of the data in the transmission process; iris image data storage At the time, the use of SM4 encryption algorithm to encrypt and store the original iris data to ensure data storage security; in addition, the system can be managed hierarchically, and different levels of authority can be assigned according to user levels to ensure application security.
SMD Common Mode Coil
SMD size 1210,1608,2012, 3216, 3225, 4532, its corresponding thickness is only 1.2 mm, 2.0 mm, 2.2 mm, and 2.8 mm, making it an ultra-thin SMD common mode inductor.
Electrical characteristics have a high differential mode cutoff frequency, common mode noise attenuation in a wide range of frequencies, making it an ideal choice for suppressing noise on ultra-high-speed signal lines, such as Display Port, DVI, USB 3.x, and HDMI 2.0 . It is also suitable for high-speed differential signal lines, such as USB, IEEE1394, LVDS, and is compatible with USB Type-C specifications.